The Complete Guide to SPF: Understanding Sender Policy Framework for Email Security
In today's digital landscape, email remains one of the most critical communication channels for businesses and individuals alike. However, it's also one of the most vulnerable to cyber attacks, including phishing, spoofing, and spam. Enter SPF (Sender Policy Framework) - a crucial email authentication protocol that serves as the first line of defense against email fraud. This comprehensive guide will explore everything you need to know about SPF, from its technical foundations to practical implementation strategies.
What is SPF (Sender Policy Framework)?
SPF, or Sender Policy Framework, is an email authentication protocol designed to prevent email spoofing and improve email deliverability. It works by allowing domain owners to specify which mail servers are authorized to send emails on behalf of their domain. Think of SPF as a "whitelist" that tells receiving mail servers which IP addresses and mail servers are legitimate senders for a particular domain.
SPF was first proposed in 2003 and became an RFC (Request for Comments) standard in 2014 as RFC 7208. It's built on the foundation of DNS (Domain Name System) records, making it a DNS-based email authentication method.
The Problem SPF Solves: Email Spoofing and Its Consequences
Understanding Email Spoofing
Email spoofing is a technique used by cybercriminals to forge the sender's address in an email header, making it appear as if the email comes from a trusted source. This is possible because the Simple Mail Transfer Protocol (SMTP), which governs email transmission, doesn't inherently verify the sender's identity.
Common Attack Vectors
- Phishing Attacks: Criminals impersonate legitimate organizations to steal credentials or sensitive information
- Business Email Compromise (BEC): Attackers impersonate executives or trusted partners to authorize fraudulent transactions
- Brand Impersonation: Malicious actors use your domain to damage your reputation and conduct scams
- Spam Distribution: Your domain becomes a vehicle for distributing unwanted content
The Business Impact
- Financial Losses: Direct fraud and incident response costs
- Reputation Damage: Loss of customer trust and brand credibility
- Legal Consequences: Regulatory compliance issues and potential lawsuits
- Operational Disruption: IT resources diverted to handle security incidents
How SPF Works: The Technical Deep Dive
The SPF Authentication Process
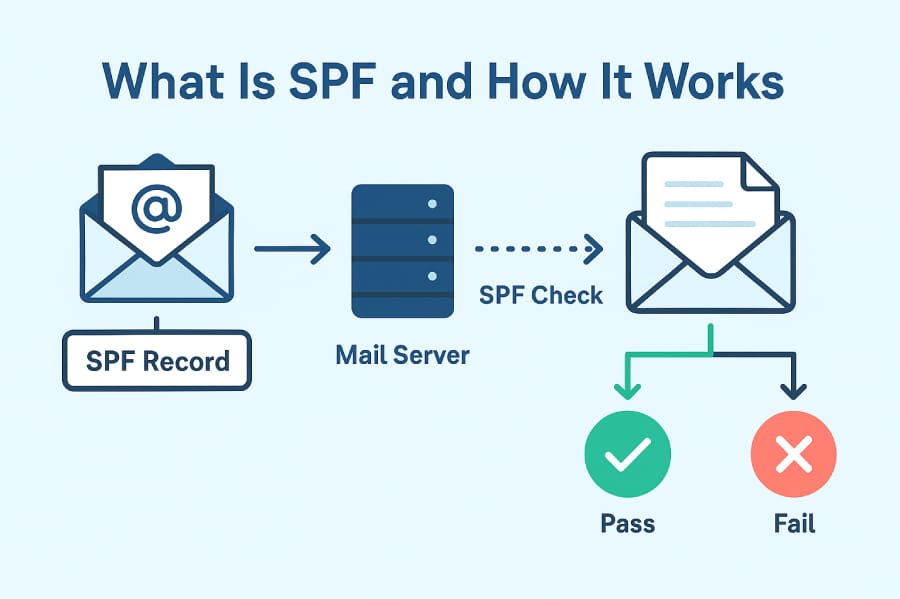
SPF operates through a systematic verification process that occurs every time an email is received:
Step 1: Email Transmission
When an email is sent, the receiving mail server captures two critical pieces of information:
- The envelope sender (also called the "return path" or "bounce address")
- The IP address of the sending mail server
Step 2: DNS Lookup
The receiving server extracts the domain from the envelope sender address and performs a DNS TXT record lookup to find the domain's SPF record.
Step 3: IP Address Verification
The receiving server compares the IP address of the sending mail server against the list of authorized IP addresses specified in the SPF record.
Step 4: Policy Enforcement
Based on the comparison result and the policy specified in the SPF record, the receiving server decides how to handle the email:
- Pass: The sending IP is authorized - email proceeds normally
- Fail: The sending IP is not authorized - action depends on the specified policy
- SoftFail: Suspicious but not rejected - typically marked as spam
- Neutral: No policy specified - no SPF-based decision made
SPF Record Structure and Syntax
SPF records are stored as DNS TXT records with a specific syntax. Here's the anatomy of an SPF record:
v=spf1 include:_spf.google.com include:mailgun.org ip4:192.168.1.100 ~all
Core Components Explained:
1. Version Declaration
v=spf1- Always the first element, specifying SPF version 1
2. Mechanisms
include:- References another domain's SPF recordip4:- Specifies individual IPv4 addresses or CIDR rangesip6:- Specifies individual IPv6 addresses or CIDR rangesa:- Authorizes the domain's A record IP addressesmx:- Authorizes the domain's MX record IP addressesexists:- Performs a DNS lookup for conditional authorization
3. Qualifiers
+(Pass) - Explicitly authorized (default if no qualifier specified)-(Fail) - Explicitly not authorized~(SoftFail) - Probably not authorized, but don't reject?(Neutral) - No policy, don't use SPF for this domain
4. The "All" Mechanism
+all- Allow all (not recommended for security)-all- Deny all not explicitly authorized (strictest policy)~all- SoftFail for all not explicitly authorized (recommended)?all- Neutral for all (equivalent to no SPF record)
Detailed SPF Implementation Guide
Phase 1: Planning and Analysis
Inventory Your Email Infrastructure
Before creating your SPF record, you must identify all systems that send email on behalf of your domain:
- Primary Mail Servers: Your organization's main email servers
- Third-Party Services: Marketing platforms (Mailchimp, Constant Contact), CRM systems (Salesforce), monitoring tools
- Web Applications: Contact forms, e-commerce platforms, notification systems
- Cloud Services: Office 365, Google Workspace, AWS SES
- Legacy Systems: Older applications that might send automated emails
Conduct an Email Flow Audit
Map out your complete email ecosystem:
- Document all outbound email sources
- Identify IP addresses and sending domains
- Note any planned changes or migrations
- Consider disaster recovery and backup systems
Phase 2: SPF Record Creation
Basic SPF Record Examples
Simple Organization with Google Workspace:
v=spf1 include:_spf.google.com ~all
Organization with Multiple Email Services:
v=spf1 include:_spf.google.com include:servers.mcsv.net include:sendgrid.net ~all
Organization with Dedicated Mail Servers:
v=spf1 ip4:203.0.113.10 ip4:203.0.113.11 include:_spf.google.com ~all
Complex Enterprise Setup:
v=spf1 include:_spf.google.com include:mailgun.org ip4:192.168.1.0/24 ip6:2001:db8::/32 ~all
Advanced SPF Configurations
Using Macros for Dynamic Records:
v=spf1 exists:%{ir}.%{v}._spf.example.com ~all
Conditional Authorization:
v=spf1 exists:%{i}._spf.%{d} include:_spf.google.com ~all
Phase 3: Implementation and Testing
DNS Record Deployment
- Create the TXT Record: Add your SPF record as a DNS TXT record for your domain
- Verify Propagation: Use tools like
digornslookupto confirm the record is published - Test Gradually: Start with a permissive policy (
~all) before moving to strict (-all)
Comprehensive Testing Strategy
1. Syntax Validation
Use SPF record checkers to validate syntax:
dig txt example.com
nslookup -type=txt example.com
2. Functional Testing
Send test emails from all authorized sources and verify they pass SPF checks.
3. Third-Party Validation Tools
- MXToolbox SPF Record Checker
- DMARCian SPF Surveyor
- Google Admin Toolbox
4. Email Authentication Headers Analysis
Examine email headers for SPF results:
Authentication-Results: mx.google.com;
spf=pass (google.com: domain of sender@example.com designates 209.85.220.69 as permitted sender)
Common SPF Implementation Challenges and Solutions
Challenge 1: The 10 DNS Lookup Limit
SPF has a built-in limit of 10 DNS lookups per SPF evaluation to prevent infinite loops and reduce server load.
Problem Scenarios:
- Multiple
include:statements - Nested SPF records with many includes
- Complex corporate email infrastructures
Solutions:
- Flattening SPF Records: Replace
include:statements with direct IP addresses - SPF Optimization Services: Use services that automatically flatten and optimize SPF records
- Domain Segmentation: Use subdomains for different email functions
Example of SPF Flattening:
Before: v=spf1 include:_spf.google.com include:mailgun.org include:servers.mcsv.net ~all
After: v=spf1 ip4:209.85.128.0/17 ip4:64.233.160.0/19 ip4:209.217.0.0/16 ~all
Challenge 2: Email Forwarding Issues
SPF can break email forwarding because the forwarding server's IP address won't be in the original domain's SPF record.
Solutions:
- SRS (Sender Rewriting Scheme): Modify the envelope sender during forwarding
- DMARC Policy Alignment: Use DKIM alongside SPF for proper authentication
- Forwarding Service Configuration: Work with forwarding services to implement SRS
Challenge 3: Managing Multiple Email Services
Organizations often use multiple email service providers, making SPF management complex.
Best Practices:
- Centralized Documentation: Maintain a comprehensive inventory of all email services
- Automated Monitoring: Use tools to monitor SPF record changes and effectiveness
- Regular Audits: Periodically review and update SPF records
- Service Provider Coordination: Work with vendors to understand their SPF requirements
SPF Best Practices and Security Considerations
Security Best Practices
1. Use Strict Policies Gradually
Phase 1: v=spf1 include:_spf.google.com ?all (neutral - monitoring)
Phase 2: v=spf1 include:_spf.google.com ~all (soft fail - typical deployment)
Phase 3: v=spf1 include:_spf.google.com -all (hard fail - maximum security)
2. Regular SPF Record Maintenance
- Monthly Reviews: Check for changes in email service providers
- Quarterly Audits: Comprehensive review of all authorized senders
- Annual Assessments: Full infrastructure review and SPF optimization
3. Monitoring and Alerting
Implement monitoring for:
- SPF authentication failures
- Unusual email sending patterns
- DNS record changes
- Service provider modifications
4. Documentation and Change Management
- Maintain detailed documentation of all authorized senders
- Implement change approval processes for SPF modifications
- Keep historical records of SPF changes
Performance Optimization
1. Minimize DNS Lookups
- Use IP addresses instead of domain names when possible
- Optimize the order of mechanisms (most common first)
- Consider SPF record flattening for complex setups
2. Regional Considerations
- Account for geographically distributed sending infrastructure
- Consider CDN and load balancer IP ranges
- Plan for disaster recovery scenarios
3. Service Provider Management
- Understand each provider's SPF requirements
- Monitor provider infrastructure changes
- Maintain direct communication channels for issues
Integration with Other Email Security Protocols
SPF + DKIM (DomainKeys Identified Mail)
While SPF authenticates the sending server, DKIM authenticates the email content through cryptographic signatures.
Combined Benefits:
- SPF validates the sending infrastructure
- DKIM ensures email content integrity
- Together they provide comprehensive authentication
Implementation Considerations:
SPF Record: v=spf1 include:_spf.google.com ~all
DKIM Record: v=DKIM1; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC...
SPF + DMARC (Domain-based Message Authentication, Reporting, and Conformance)
DMARC builds upon SPF and DKIM to provide policy enforcement and reporting.
DMARC Policy Examples:
v=DMARC1; p=none; rua=mailto:dmarc@example.com
v=DMARC1; p=quarantine; rua=mailto:dmarc@example.com; pct=50
v=DMARC1; p=reject; rua=mailto:dmarc@example.com
SPF Alignment in DMARC:
- Strict Alignment: Exact domain match required
- Relaxed Alignment: Subdomain matches accepted
Advanced SPF Topics
SPF Macros and Dynamic Records
SPF supports macros for dynamic record evaluation:
Common Macros:
%{i}- Sender IP address%{d}- Current domain%{s}- Sender email address%{h}- HELO/EHLO domain
Advanced Macro Example:
v=spf1 exists:%{ir}.%{v}._spf.%{d} ~all
SPF for Subdomains
Subdomains don't inherit parent domain SPF records:
Subdomain SPF Strategy:
example.com: v=spf1 include:_spf.google.com ~all
mail.example.com: v=spf1 ip4:203.0.113.10 ~all
blog.example.com: v=spf1 include:_spf.wordpress.com ~all
Handling IP Address Changes
Strategies for Dynamic IP Environments:
- Use Service Provider Includes: Rely on
include:statements for cloud services - CIDR Ranges: Use network ranges instead of individual IPs
- Automated Updates: Implement scripts to update SPF records automatically
Troubleshooting Common SPF Issues
Issue 1: Legitimate Emails Failing SPF
Symptoms:
- Legitimate emails marked as spam
- SPF fail results in email headers
- Complaints from recipients about missing emails
Troubleshooting Steps:
- Verify the sending IP against your SPF record
- Check for recent infrastructure changes
- Review third-party service configurations
- Analyze email headers for detailed SPF results
Solution Example:
# Check current SPF record
dig txt example.com
# Verify IP authorization
# If 203.0.113.50 is sending but not authorized, add it:
v=spf1 include:_spf.google.com ip4:203.0.113.50 ~all
Issue 2: SPF Record Not Found
Symptoms:
- "SPF record not found" errors
- Inconsistent email delivery
- DNS lookup failures
Troubleshooting Steps:
- Verify DNS record publication
- Check DNS propagation globally
- Ensure correct record format
- Test with multiple DNS servers
Issue 3: Too Many DNS Lookups
Symptoms:
- SPF evaluation errors
- "Too many DNS lookups" messages
- Inconsistent authentication results
Resolution Strategy:
- Count current DNS lookups in your SPF record
- Identify candidates for flattening
- Implement SPF optimization
- Monitor after changes
Measuring SPF Effectiveness
Key Performance Indicators (KPIs)
1. Authentication Success Rate
- SPF Pass Rate: Percentage of legitimate emails passing SPF
- False Positive Rate: Legitimate emails failing SPF
- False Negative Rate: Malicious emails passing SPF
2. Security Metrics
- Spoofing Attempt Detection: Number of SPF failures from unauthorized sources
- Brand Protection: Reduction in brand impersonation attempts
- Threat Intelligence: Analysis of attack patterns
3. Operational Metrics
- Email Deliverability: Improvement in inbox placement rates
- DNS Performance: SPF lookup response times
- Maintenance Overhead: Time spent managing SPF records
Reporting and Analysis Tools
1. Built-in Email Platform Reports
Most email platforms provide SPF reporting:
- Google Workspace: Email security reports
- Microsoft 365: Threat protection reports
- Third-party services: Platform-specific analytics
2. DMARC Aggregate Reports
When DMARC is implemented, aggregate reports provide detailed SPF performance data:
<record>
<row>
<source_ip>203.0.113.10</source_ip>
<count>150</count>
<policy_evaluated>
<disposition>none</disposition>
<dkim>pass</dkim>
<spf>pass</spf>
</policy_evaluated>
</row>
</record>
3. Third-Party Monitoring Services
- DMARCian
- Agari (now part of Fortra)
- Proofpoint Email Fraud Defense
- Valimail
Future of SPF and Email Authentication
Emerging Trends
1. BIMI (Brand Indicators for Message Identification)
BIMI builds on SPF, DKIM, and DMARC to display brand logos in email clients for authenticated messages.
2. Enhanced DNS Security
- DNSSEC integration for SPF records
- DNS over HTTPS (DoH) and DNS over TLS (DoT) support
- Improved DNS resilience and security
3. AI and Machine Learning Integration
- Automated SPF record optimization
- Intelligent threat detection and response
- Predictive email security analytics
Regulatory and Compliance Considerations
1. Data Protection Regulations
- GDPR implications for email security logging
- CCPA requirements for email data handling
- Industry-specific compliance mandates
2. Government and Industry Standards
- NIST Cybersecurity Framework alignment
- Industry best practice evolution
- International cooperation on email security
Conclusion: Building a Robust Email Security Foundation
SPF represents a fundamental component of modern email security architecture. While it's not a silver bullet against all email-based threats, when properly implemented and maintained, SPF provides crucial protection against domain spoofing and significantly improves email deliverability.
Key Takeaways for Success
- Start with Proper Planning: Thoroughly understand your email infrastructure before implementing SPF
- Implement Gradually: Begin with permissive policies and gradually tighten security
- Monitor Continuously: Regular monitoring and maintenance are essential for long-term success
- Integrate Comprehensively: Combine SPF with DKIM and DMARC for maximum protection
- Stay Current: Keep up with evolving threats and best practices in email security
The Path Forward
As email continues to evolve as a critical business communication channel, the importance of robust authentication mechanisms like SPF will only grow. Organizations that invest in proper SPF implementation today will be better positioned to protect their users, maintain their reputation, and ensure reliable email communication in an increasingly complex threat landscape.
Remember that email security is not a one-time implementation but an ongoing process that requires attention, maintenance, and continuous improvement. By following the comprehensive guidelines outlined in this blog post, you'll be well-equipped to implement and maintain effective SPF protection for your organization's email infrastructure.