DMARC Explained: Your Complete Guide to Email Domain Protection
Email spoofing is one of the most common attack vectors used by cybercriminals today. Attackers impersonate legitimate domains to trick recipients into believing fraudulent emails are genuine. DMARC (Domain-based Message Authentication, Reporting, and Conformance) is the solution that puts you back in control of your email domain.
What Exactly is DMARC?
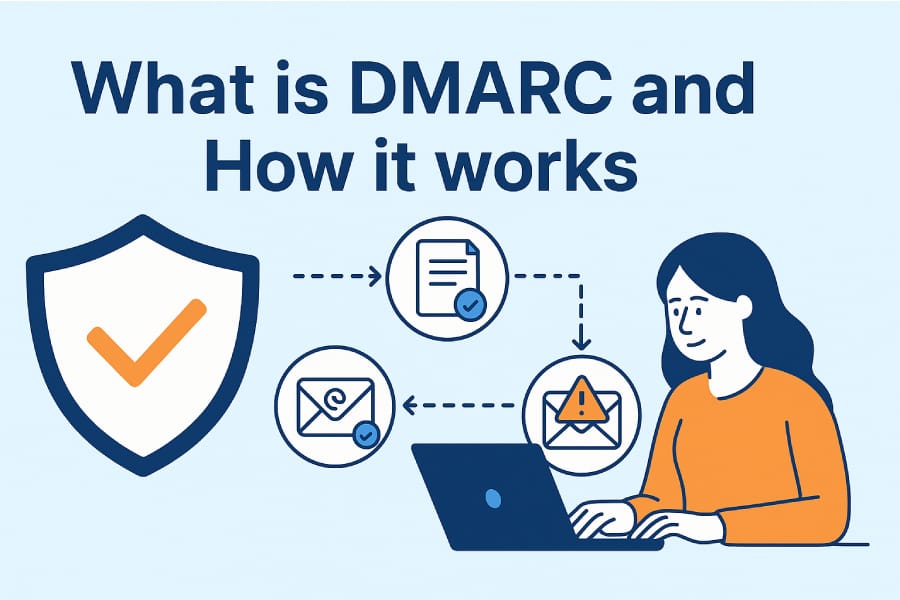
DMARC is an email validation system designed to detect and prevent email spoofing. It acts as a bridge between two existing email authentication protocols - SPF and DKIM - while adding crucial policy enforcement and reporting capabilities.
Imagine DMARC as a bouncer at an exclusive club. It checks the ID of every email claiming to be from your domain, verifies it against your guest list (SPF/DKIM), and then follows your specific instructions on what to do with imposters.
The Three Pillars of DMARC
1. Authentication
DMARC relies on existing authentication methods:
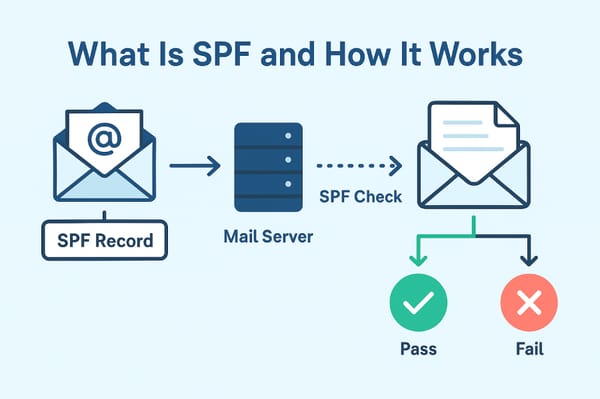
- SPF: Verifies the sending server is authorized
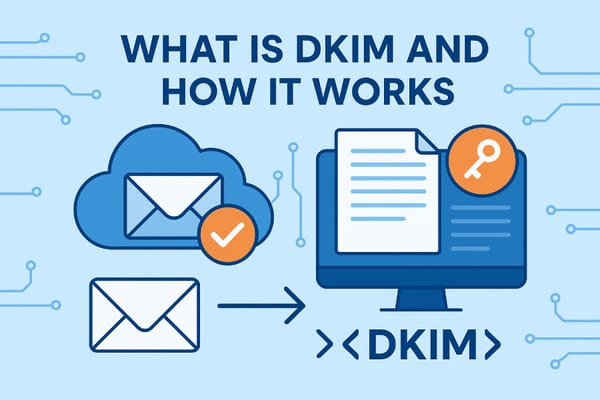
- DKIM: Confirms the email hasn't been tampered with using cryptographic signatures
2. Alignment
This is DMARC's secret weapon. Even if an email passes SPF or DKIM, DMARC checks if the authenticated domain matches the "From" address that recipients see. This prevents sophisticated spoofing techniques.
3. Policy Enforcement
DMARC lets you tell receiving email servers exactly what to do when authentication fails:
- Monitor and report only
- Send suspicious emails to spam
- Reject fraudulent emails completely
How DMARC Actually Works
Here's what happens when someone receives an email claiming to be from your domain:
- The email arrives at the recipient's mail server
- SPF check - Is the sending server authorized?
- DKIM check - Is the digital signature valid?
- DMARC alignment - Does the authenticated domain match the "From" address?
- Policy lookup - What does the domain owner want us to do?
- Action taken - Follow the policy (none, quarantine, or reject)
- Report sent - Inform the domain owner what happened
Complete DMARC Tag Reference
DMARC policies are published as DNS TXT records. Here's every tag you need to know:
| Tag | Description | Values | Required | Example |
|---|---|---|---|---|
| v | DMARC version | DMARC1 | Yes | v=DMARC1 |
| p | Policy for domain | none, quarantine, reject | Yes | p=reject |
| sp | Policy for subdomains | none, quarantine, reject | No | sp=quarantine |
| rua | Aggregate report URI | mailto: address | No | rua=mailto:reports@example.com |
| ruf | Forensic report URI | mailto: address | No | ruf=mailto:forensic@example.com |
| adkim | DKIM alignment mode | r (relaxed), s (strict) | No | adkim=s |
| aspf | SPF alignment mode | r (relaxed), s (strict) | No | aspf=s |
| pct | Percentage of messages | 0-100 | No | pct=100 |
| fo | Forensic options | 0, 1, d, s | No | fo=1 |
| rf | Report format | afrf | No | rf=afrf |
| ri | Report interval | seconds | No | ri=86400 |
Detailed Tag Explanations
Policy Tags (p, sp)
none: No action, just monitor and reportquarantine: Mark as spam/suspiciousreject: Block the email completely
Alignment Tags (adkim, aspf)
relaxed: Allows subdomain alignment (mail.example.com aligns with example.com)strict: Requires exact domain match
Forensic Options (fo)
0: Generate reports if all authentication fails1: Generate reports if any authentication failsd: Generate reports if DKIM failss: Generate reports if SPF fails
Real-World DMARC Examples
Basic Monitoring Policy
v=DMARC1; p=none; rua=mailto:dmarc@example.com
Perfect for getting started - monitors everything, blocks nothing
Balanced Protection
v=DMARC1; p=quarantine; sp=reject; rua=mailto:dmarc@example.com; pct=50
Quarantines suspicious domain emails, rejects subdomain spoofs, applies to 50% of messages
Maximum Security
v=DMARC1; p=reject; rua=mailto:dmarc@example.com; ruf=mailto:forensic@example.com; adkim=s; aspf=s; pct=100
Rejects all unauthenticated emails with strict alignment
Implementation Roadmap
Week 1-2: Intelligence Gathering
Deploy monitoring policy (p=none) to understand your email ecosystem. Identify all legitimate senders.
Week 3-4: Fine-Tuning
Fix SPF/DKIM issues for legitimate senders. Ensure all authorized sources authenticate properly.
Week 5-6: Gradual Enforcement
Move to quarantine policy (p=quarantine) with percentage rollout (pct=25, then pct=50, then pct=100).
Week 7+: Full Protection
Implement reject policy (p=reject) once confident in your authentication setup.
Common Mistakes to Avoid
Rushing to Reject Policy
Many organizations jump straight to p=reject and break legitimate email flow. Always start with monitoring.
Ignoring Subdomains
Attackers often target subdomains. Use the sp tag to protect them separately.
Overlooking Third-Party Senders
Marketing platforms, CRM systems, and notification services need proper authentication setup.
Not Analyzing Reports
DMARC reports contain valuable security intelligence. Regularly review them for threats and misconfigurations.
Reading DMARC Reports
DMARC generates two types of reports:
Aggregate Reports (RUA)
Daily summaries showing authentication results, sources, and policy actions. These help you understand legitimate vs. malicious traffic patterns.
Forensic Reports (RUF)
Real-time alerts for specific authentication failures. Useful for investigating suspected attacks or misconfigurations.
Why DMARC Matters More Than Ever
Business Email Compromise (BEC) attacks cost organizations billions annually. Most start with domain spoofing.
Brand Protection becomes critical as customers increasingly scrutinize email authenticity.
Regulatory Compliance in many industries now requires email authentication measures.
Deliverability Benefits mean your legitimate emails are more likely to reach inboxes instead of spam folders.
Advanced DMARC Strategies
Subdomain Segregation
Use different policies for different subdomain purposes:
_dmarc.marketing.example.com: v=DMARC1; p=quarantine
_dmarc.noreply.example.com: v=DMARC1; p=reject
Gradual Rollout with Percentage
Test policy changes on a subset of traffic:
v=DMARC1; p=reject; pct=10; rua=mailto:dmarc@example.com
Multiple Report Destinations
Send reports to different teams:
v=DMARC1; p=quarantine; rua=mailto:security@example.com,mailto:it@example.com
Tools and Resources
DMARC Record Generators
Many online tools help create properly formatted DMARC records.
Report Analyzers
Third-party services can parse and visualize DMARC reports for easier analysis.
Testing Tools
Use email authentication checkers to verify your DMARC implementation.
The Bottom Line
DMARC isn't just another IT security checkbox - it's your shield against email-based attacks that could devastate your organization. The implementation process requires patience and careful planning, but the protection it provides is invaluable.
Start with monitoring, learn from the reports, fix authentication issues, and gradually increase protection levels. Your future self (and your customers) will thank you when the next wave of email attacks hits and bounces harmlessly off your DMARC-protected domain.
Remember: every day without DMARC is another day attackers can freely impersonate your domain. The question isn't whether you can afford to implement DMARC - it's whether you can afford not to.
Ready to implement DMARC? Start with a simple monitoring policy today and begin your journey toward email security.