DKIM: DomainKeys Identified Mail - Complete Guide
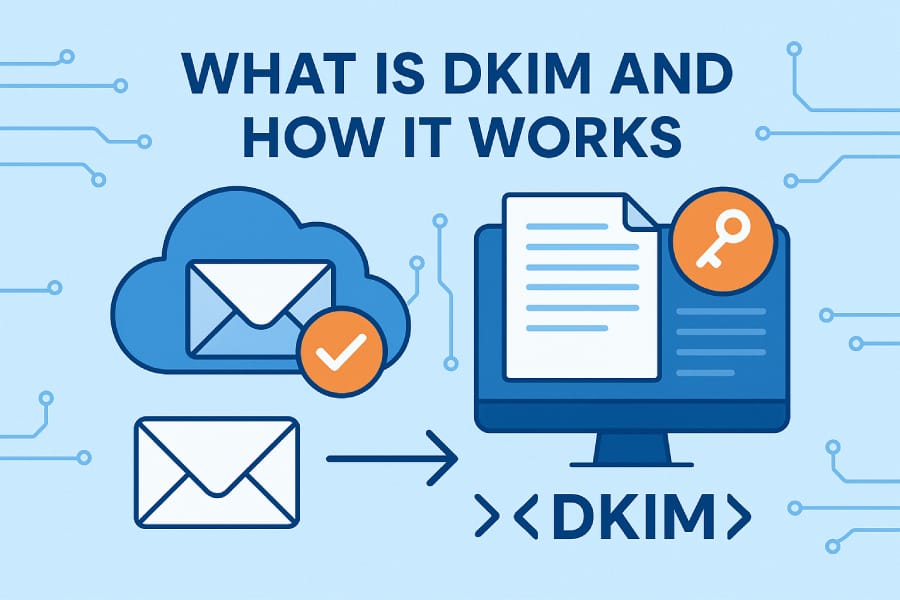
What is DKIM?
DKIM (DomainKeys Identified Mail) is an email authentication protocol that allows email recipients to verify that an email message was actually sent by the domain it claims to be from and that the message hasn't been tampered with during transmission. It's a crucial component of modern email security infrastructure.
DKIM works by adding a digital signature to email headers, which can be validated against a public key published in the sender's DNS records. This cryptographic approach helps combat email spoofing, phishing attacks, and ensures email integrity.
Key Components of DKIM
1. Digital Signatures
- Uses public-key cryptography (typically RSA or Ed25519)
- Private key signs outgoing emails
- Public key validates incoming emails
2. DNS Records
- Public keys are published as TXT records in DNS
- Format:
selector._domainkey.domain.com - Contains the public key and policy information
3. DKIM Headers
DKIM-Signatureheader added to outgoing emails- Contains signature algorithm, selector, domain, and signature data
How DKIM Works: Step-by-Step Process
Phase 1: Setup and Configuration
-
Key Pair Generation
- Domain owner generates a public/private key pair
- Private key stored securely on the mail server
- Public key published in DNS
-
DNS Publication
selector1._domainkey.example.com IN TXT "v=DKIM1; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC..." -
Mail Server Configuration
- Configure mail server to sign outgoing emails
- Specify which headers to include in signature
- Set up selector and signing domain
Phase 2: Email Signing (Outbound)
-
Message Preparation
- Email server prepares the outgoing message
- Identifies headers to be signed (From, Subject, Date, etc.)
-
Canonicalization
- Normalizes headers and body content
- Handles whitespace and line ending differences
- Two algorithms: Simple and Relaxed
-
Hash Creation
- Creates hash of selected headers and body
- Typically uses SHA-256 algorithm
-
Digital Signing
- Signs the hash using the private key
- Generates the DKIM-Signature header
- Adds signature to the email
Phase 3: Email Verification (Inbound)
-
Signature Extraction
- Receiving server extracts DKIM-Signature header
- Parses signature parameters (domain, selector, algorithm)
-
Public Key Retrieval
- Queries DNS for the public key
- Uses selector and domain from signature
dig TXT selector._domainkey.domain.com
-
Signature Verification
- Recreates hash using same canonicalization method
- Verifies signature using public key
- Compares with original signature
-
Result Processing
- Pass: Signature is valid
- Fail: Signature is invalid or missing
- Neutral: No signature or policy neutral
DKIM Signature Header Breakdown
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed;
d=example.com; s=selector1; t=1634567890;
bh=2jUSOH9NhtVGCQWNr9BrIAPreKQjO6Sn7XIkfJVOzv8=;
h=From:To:Subject:Date:Message-ID;
b=dzdVyOfAKCdLXdJOc9G2q8LoXSlEniSbav+yuU4zGiM...
Parameter Explanation:
- v: Version (always "1")
- a: Algorithm (rsa-sha256, rsa-sha1, ed25519-sha256)
- c: Canonicalization (simple/simple, relaxed/relaxed, etc.)
- d: Signing domain
- s: Selector
- t: Timestamp
- bh: Body hash
- h: Signed headers
- b: Signature data
DNS Record Configuration
Basic DKIM DNS Record Structure:
selector._domainkey.domain.com. IN TXT "v=DKIM1; k=rsa; p=publickey"
Complete Example:
default._domainkey.example.com. IN TXT (
"v=DKIM1; "
"k=rsa; "
"t=s; "
"p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDGQ2jKhWmLdY+hUJNQ..."
)
DNS Record Parameters:
- v: Version identifier
- k: Key type (rsa, ed25519)
- t: Testing mode (s=strict, y=testing)
- p: Public key data (base64 encoded)
- h: Hash algorithms (sha1, sha256)
- s: Service type (* or email)
Security Benefits
1. Authentication
- Verifies the sending domain's identity
- Prevents domain spoofing attacks
- Establishes sender reputation
2. Integrity
- Ensures message hasn't been modified
- Detects tampering during transmission
- Protects against man-in-the-middle attacks
3. Non-repudiation
- Provides proof of message origin
- Supports forensic investigations
- Enables audit trails
Common Implementation Challenges
1. Key Management
- Secure private key storage
- Regular key rotation
- Backup and recovery procedures
2. DNS Configuration
- Proper record formatting
- Multiple selector management
- TTL considerations
3. Mail Server Setup
- Header selection policies
- Canonicalization choices
- Integration with existing systems
DKIM Policy and Best Practices
1. Key Rotation
- Rotate keys every 6-12 months
- Use multiple selectors for smooth transitions
- Monitor for compromised keys
2. Header Selection
- Always sign From header
- Include Subject, Date, Message-ID
- Consider To, CC for additional security
3. Testing and Monitoring
- Use testing mode initially (t=y)
- Monitor DKIM verification rates
- Set up failure notifications
4. Integration with SPF and DMARC
- Combine with SPF for comprehensive protection
- Use DMARC to define policy actions
- Achieve email authentication alignment
Troubleshooting Common Issues
1. Signature Verification Failures
- Check DNS record syntax
- Verify key pair matching
- Review canonicalization settings
2. DNS Resolution Problems
- Confirm DNS propagation
- Check record formatting
- Validate selector names
3. Mail Server Configuration
- Review signing policies
- Check header selections
- Verify timestamp accuracy
Tools for DKIM Testing
1. Command Line Tools
# Check DKIM DNS record
dig TXT selector._domainkey.example.com
# Test DKIM signature
opendkim-testkey -d example.com -s selector
2. Online Validators
- MXToolbox DKIM Checker
- DKIM Validator
- Mail-tester.com
3. Email Headers Analysis
- Review Authentication-Results headers
- Check DKIM-Signature parameters
- Analyze verification outcomes
Conclusion
DKIM is a fundamental email security protocol that provides authentication and integrity verification for email messages. When properly implemented alongside SPF and DMARC, it creates a robust defense against email-based attacks. Regular monitoring, proper key management, and adherence to best practices ensure maximum effectiveness of DKIM deployment.
The protocol's cryptographic foundation makes it highly reliable for verifying email authenticity, making it an essential component of modern email security infrastructure.